Data Leak Prevention Through PAM
Introduction
In today’s world, where everyone is always connected to internet and with the growth of IT industries, the value of data for specific user or an organization is the most important asset. This confidential data, whether corporate or customer-related, can be leaked from almost any computing device today, including physical and virtual servers, databases, end user equipment, flash storage devices, and mobile devices.
This kind of unauthorized access transmission or of data from within an organization to an external destination or recipient is termed as “Data leakage” or “Data Breach”. With such huge amount of data generated, there hardly would be a day that goes without a confidential data breach hitting the headlines.
What is Data Leak?
In today’s world, where everyone is always connected to internet and with the growth of IT industries, the value of data for specific user or an organization is the most important asset. This confidential data, whether corporate or customer-related, can be leaked from almost any computing device today, including physical and virtual servers, databases, end user equipment, flash storage devices, and mobile devices.
This kind of unauthorized access transmission or of data from within an organization to an external destination or recipient is termed as “Data leakage” or “Data Breach”. With such huge amount of data generated, there hardly would be a day that goes without a confidential data breach hitting the headlines.
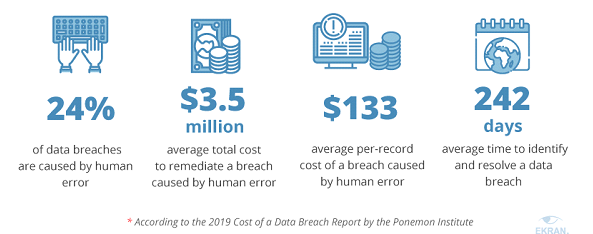
The Accidental Data Leak
Data leaks are not always intentional or malicious, in fact majority of them are occurred due to sheer negligence.
For example, an employee forgets to lock the system and leaves the desk. Any other person can now get access to the data, even though it was unintentional still can result in the penalties and reputational damage as they have ignored legal responsibilities.
Data Leak via Electronic Communications
As organizations give employees access to the internet email, and instant messaging as part of their role. All these sources are capable of file transfer or accessing external sources over the internet which creates the problem.
For example, a cybercriminal could easily spoof a business email account and request sensitive or confidential information to be sent to them. The user would unintentionally send the information, which could contain financial data or sensitive pricing information.
Privileged or Business Users
One of the major yet unnoticed type of data leaks happens within the organization is by their own trusted employees. Reason for that may be personal grievances with the organization, promotion or better job opportunity at other rival organization or just an intent to harm company reputation could be another reason for data leaks.
This is the most dangerous type of data leak as it’s very difficult to find the culprits in this scenario. The privileged users are having access to critical assets of the organization. If the assets are not monitored and they can add malicious software or extract valuable information which would cost millions to the company
These insider privileged data leaks are mostly not noticed and there are not proper prevention measures to keep track of the privileged user in terms of data that they transfer between the servers and also from servers to their desktops and vice versa. File, folder deletion or moving is also a challenge which brings systems down at times.
Data Leak Through Privileged Accesses
Data Leak Prevention (DLP) is the practice of finding and preventing data breaches, unwanted destruction of valuable information. Organizations worldwide use DLP to protect and secure their data and comply with regulations.
There are different various DLP methods used by different organizations which help in the below things:
- Protect Intellectual Property critical for the organization.
- Achieve data visibility in large organizations.
- Helps prevent lawsuits, loss of reputation, loss of credibility, loss of revenue.
- Secure data on remote cloud systems.
Even after so many efforts for data leak prevention the most important aspect is overshadowed which is Privileged user’s threat.
Privileged users have a high level access to important resources and have understanding of organization’s structural and functional work methods. These users are usually administrators but can also be managers or other business users. In order to prevent privileged user abuse, it’s critical to monitor those who supervise your systems.
How
Iraje PAM Solution
helps in
Insider Threat Detection?
Iraje PAM Privileged Access Management protects enterprise assets from the growing risk of data leaks. It helps business to manage, monitor, and control privileged users to avoid sensitive data leak.
The standard PAM features combined with DLP features makes Iraje a better solution for getting visibility and control on privileged accesses. Conclusion
Apart from the standard PAM capabilities Iraje has interesting capabilities in PAM that helps Data Leak Prevention and tracking of all file transfers, file deletions and file movements within the enterprise environment done by privileged users. The iDLP report of Iraje PAM provides full details of all such activities done by the privileged user for forensic and root cause analysis.